From data breaches to malwares, cybersecurity is in the headlines almost every day and has become a major concern. Especially in the context of the health crisis, cyberattacks are affecting companies of all sizes. How can you prepare for cyberattacks?
We selected some current cybersecurity statistics, in order to know the current trends of threats in 2021. To prepare to face cyberattacks, a pentest is a very effective solution to strengthen your security.
2021 web, mobile, IoT, social engineering cybersecurity statistics: what is the situation?
Cybersecurity statistics and cost of data breaches
The general impression is that cyberattacks are on the rise, but are they really?
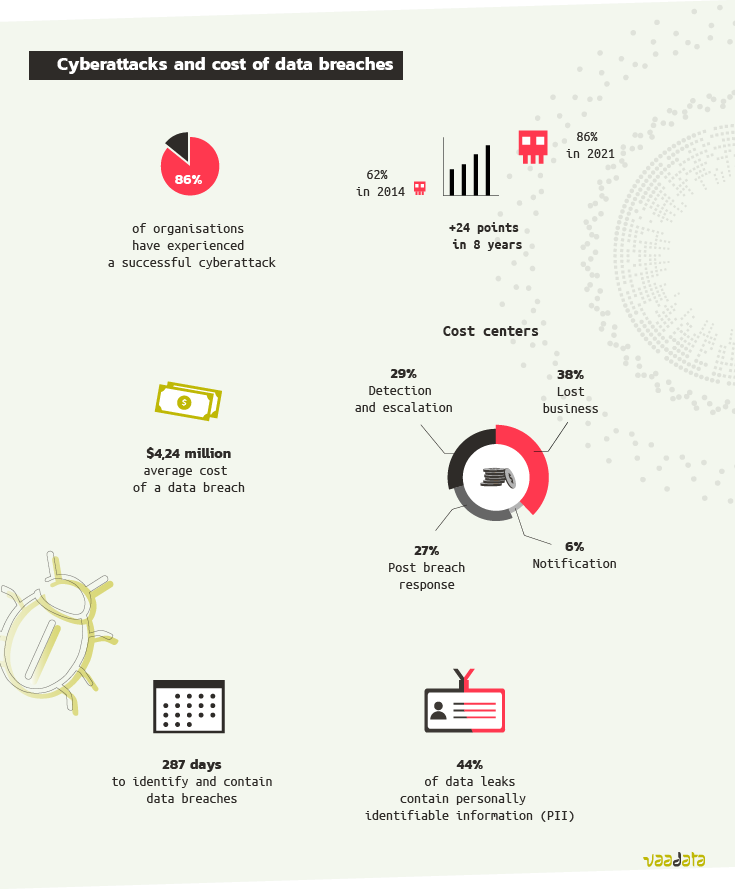
According to the Cyberedge Report [1], 86% of organisations have experienced at least one successful cyberattack in 2020. More than 4 out of 5 companies!
In the first edition of the report, in 2014, ‘only’ 62% had suffered a successful attack, an increase of 24 points in 8 years. This increase is impressive.
What is the cost of a data breach?
Cyberattacks often mean data breaches. The Cost of a Data Breach Report [2] shows that data breaches are identified on average in 212 days (7 months) and contained in 75 days. It notes that 44% of data leaks contain personally identifiable information.
The most frequent initial attack vectors for data leaks are: compromised credentials in 20% of breaches, phishing in 17% of breaches and cloud misconfigurations in 15% of breaches.
The average cost of a data breach reaches $4.24 million. Costs of a breach are divided into four cost centres:
- Lost business: 38%,
- Detection and escalation: 29% of costs (activities that enable to detect the breach)
- Post breach response: 27% of costs (redress activities to victims and regulators)
- Notification: 6% of costs.
Actions have shown to be effective in lowering the cost of a data breach. The most effective mitigating factor is to test the incident response plan (-7.7%). Other measures are business continuity management (-7.2%), red team testing (-6.3%), employee training (-6.2%), vulnerability testing (-4.5%)… [3]
Penetration testing is indeed one of the most effective tools to reduce the impact of cyberattacks, as it involves simulating an attack using the same tools and techniques as a malicious attacker.
Focusing on SME cybersecurity
SMEs and mid-sized companies also face many threats. The DBIR[4] has categorised the most frequent type of attacks according to the size of the organisation. Thus, system intrusions (attacks requiring several steps, with movement in the environment), errors and basic web applications attacks represent 80% of the types of attacks leading to data breaches for SMEs, and 74% for large companies.
Attacks against SMEs are primarily aimed at financial gain, in 93% of cases.
SMEs face external attacks, but also insider threats, which are the cause of 44% of attacks.
Risky behaviours for the management of passwords or secrets
Whether they are in small or very large companies, some people still manage their passwords or secrets insecurely.
A third of those surveyed admit to using their employer’s name in a work-related password. 1/3 use the name or birthday of their significant other, 1/3 use the name or birthday of their child [5].
54% use the same password on multiple work accounts [6].
When it comes to managing secrets, the situation is just as delicate. 80% of companies surveyed by 1Password[7] admit to not managing their secrets well.
For example, 48% of companies use a shared document or spreadsheet, with or without restricted access, to store and manage their corporate secrets.
77% of former IT/DevOps employees still have access to their former company’s infrastructure secrets.
The Covid-19 pandemic has not helped to reverse the trend, with the fast deployment of general work-from-home and the mixing of uses on both work and personal devices. Indeed, 42% of respondents use their work device every day for personal reasons when working remotely [6].
Facing ransomware attacks: key statistics
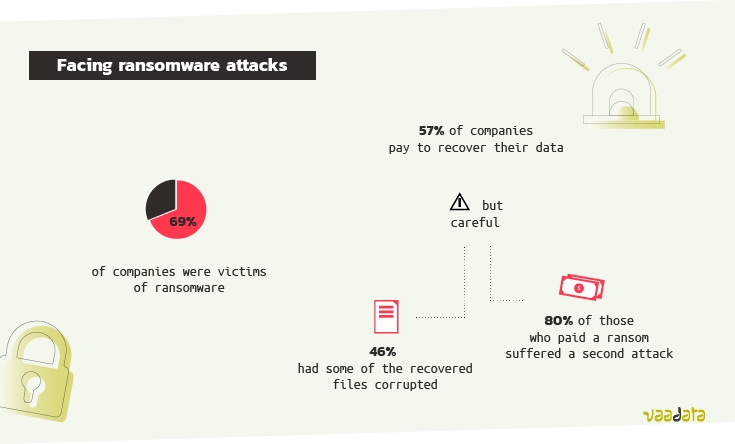
69% of companies were victims of ransomware last year [1]. The Cyberedge report also tells us that more than half of companies (57%) pay to recover its data.
A vicious circle has been set up: increasingly, when the ransom demand is paid, the data is recovered (72% of cases in 2021 – compared to 49% in 2018). Companies are therefore increasingly tempted to pay the ransom, as they see that this allows them to recover encrypted data. Ransom payments fuel the business of cybercriminals, who continue to carry out these attacks, leading to new victims, who will be tempted to pay the ransom to get its data back, etc. etc.
However, of those who paid to recover its data, 46% had some of the recovered files corrupted [8].
And double trouble, 80% of those who paid a ransom reported suffering a second ransomware attack. In 46% of cases, victims believe it was the same attackers [8].
In response to the rise in ransomware attacks, insurers have developed cyber insurance. Half of this insurance is used to cover consulting and third-party legal services. In 36% of cases, the insurance covered the cost of restitution to victims. Only 10% of organisations used their insurance to cover the cost of the ransom [4].
Web and mobile applications statistics
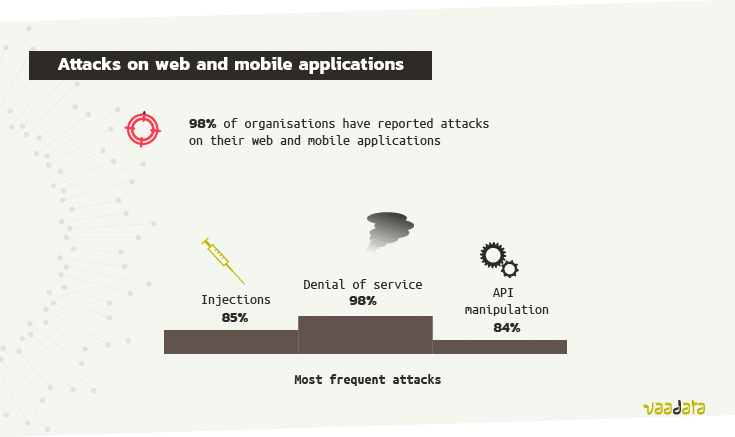
Web and mobile are not spared from cyberattacks: 98% of organisations have reported attacks on their web and mobile applications [9].
Regarding mobile applications, 42% of organisations say they have either ‘bolted-on’ security, or no security (22%).
The most frequent attacks on applications and/or web servers are:
- Denial-of-Service (DoS) attacks, reported by 89% of organisations,
- Injection attacks, reported by 85% of organisations,
- API manipulation, reported by 84% of organisations,
- Bot attacks, reported by 82% of organisations.
This is confirmed when looking at the 2021 CWE Top 25. This ranking identifies the most frequently encountered types of vulnerabilities. In the top 3, we find Out-of-bounds writing, Cross-Site-Scripting (XSS) vulnerabilities and Improper Input Validation.
The most frequent attacks on APIs are [9]:
- Denial-of-Service (DoS) attacks, reported by 87% of organisations,
- Injection attacks, 80%,
- Access violations and brute force/credential stuffing, 74%.
To facilitate development, teams rely on third-party libraries. However, in 79% of cases, these libraries are never updated once integrated into the code, whereas 92% of vulnerabilities in libraries can be remedied by an update [10].
Web and mobile applications are at the heart of business activities and have become a favourite target for attackers. They are used for a wide variety of functions, often process sensitive data and are particularly exposed. To protect yourself, performing a web application pentest can test how these applications would stand up to cyberattacks and then strengthen their security level.
IoT security statistics: a cybersecurity to strengthen
The internet of things is taking off: 11% of households have one or more smart objects [11]. But the security of connected objects is still the weak point in IoT development strategies.
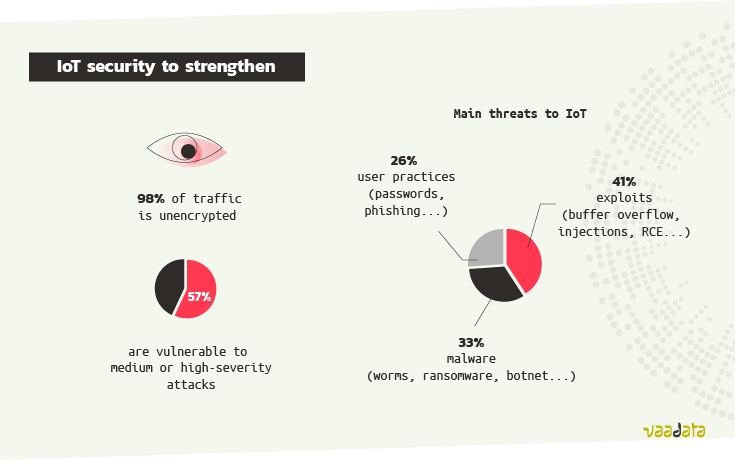
Unit 42[12] estimates that 98% of all connected object traffic is unencrypted and that more than half of all devices are vulnerable to medium or high-severity attacks.
The main threats to IoT are:
- 41%, exploits (buffer overflow, injections, RCE…)
- 33%, malware (worms, ransomware, trojans, botnets…)
- 26%, user practices (passwords, phishing…)
This is reflected in the new vulnerabilities reported in ICS Advisories, where memory corruption errors are the most frequent, accounting for 58% of cases (out-of-bounds read, out-of-bounds write, stack-based buffer overflow) [13].
To test for firmware, hardware and communications vulnerabilities, an IoT pentest typically looks for flaws in the entire ecosystem of a connected device.
Social engineering statistics: phishing, vishing and other attacks
In addition to attacks on technical vulnerabilities, cyberattacks are increasingly targeting the human factor. Attackers try to manipulate people to obtain sensitive information or to make them perform actions that compromise security.
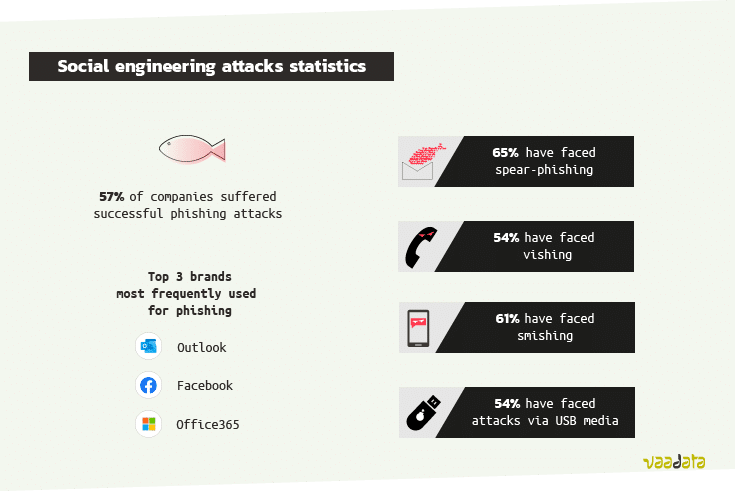
Phishing is the best-known attack. It can be sent massively to as many email addresses as possible in the attackers’ files. In 2020, 57% of companies suffered successful phishing attacks, according to Proofpoint[14].
The consequences of a successful phishing attack are data loss in 60% of cases, ransomware infection (47%) and wire fraud/financial loss in 18% of situations.
The brands most frequently used in phishing emails are Outlook, Facebook, Office 365, Paypal and Chase Personal Banking [15].
But now we are seeing a rise in targeted attacks, where a pretext or set-up is specifically designed for a particular company. Last year, 66% of organisations experienced targeted attack attempts (spear-phishing) and 65% experienced President’s scam attempts (Business Email Compromise attacks) [14].
Other attack vectors are also increasingly being used:
- 61% of companies have faced smishing attacks (phishing by sms),
- 54% of vishing attacks (phishing by telephone),
- 54% of attacks via USB media.
Social engineering remains an unknown threat. Teams are beginning to be aware of these forms of attack, but this needs to be reinforced.
- 77% know that a url can be disguised in emails,
- 55% know that an email can appear to come from someone other than the real sender,
- 58% know an attachment can be infected [14].
This is still not enough in the face of various forms of attack, and security managers believe that low security awareness is the number one barrier to IT security [1].
To increase awareness, social engineering training exists. A social engineering pentest can also help raise awareness by simulating concrete attack situations.
Performing pentests to identify vulnerabilities and strengthening your cybersecurity
As we have just seen, current cyberattacks have a very high success rate, with multiple consequences. They are aiming at both private and public structures. They seek to break into a specific target (web applications, mobile phone, connected objects, etc.) or target a company’s information system. To protect yourself against them, penetration testing is an opportunity to perform realistic attacks to determine the risk level of the target.
A pentest is a security audit following a rigorous methodology to identify all vulnerability. It detects security flaws in the targeted application or system, to establish where attackers could get in and what they could get. Technical, logical and human vulnerabilities are researched.
After the tests, a report details the vulnerabilities found as well as remediation suggestions. It can be used directly by technical teams. This allows you to fix vulnerabilities before they are exploited by real cyber attackers.
A pentest to prepare for and counter cyberattacks
Each pentest is tailored to the security challenges of the target. Whether you are an SMB, a start-up or a large company, we define the scope and duration of the audit according to the threats and your security priorities. We can focus tests on a particularly at risk element (a software, a web portal…) or conduct a global pentest, in order to test the whole information system.
A pentest can be performed in black box, grey box or white box. These different approaches correspond to different levels of information transmitted to the pentesters. It is totally possible to choose different approaches depending on the targets and the security maturity of the company on the different scopes.
To guide you in defining a pentest strategy, you can consult our white paper How to define the scope of a pentest.
Pentests are conducted on different types of targets (web, mobile, IoT, infrastructure, information system) and identify technical flaws specific to each target. For example, a web pentest will evaluate the security of servers, of the back-office, of the application layer. A mobile pentest will test iOS and Android applications. And so on.
But a pentest can also detect other weaknesses, such as using weak passwords (through brute force attacks).
In addition, to test human behaviours, it is possible to perform a social engineering pentest. This allows you to specifically test the reflexes of your teams when facing cyberattacks such as phishing, receiving ransomware or CEO fraud.
At Vaadata, we democratise penetration testing with offers adapted to startups as well as large companies. Do not hesitate to contact us to discuss your situation.
Sources:
[1] 2021 Cyberthreat Defense Report – Cyberedge Group
[2] 2021 Cost of a Data Breach Report – IBM
[3] 2020 Cost of a Data Breach Report – IBM
[4] 2021 Data Breach Investigation Report – Verizon
[5] 2021 Workplace Password Malpractice Report – Keeper Security
[6] Cybersecurity in the work from anywhere area – Yubico
[7] Hiding in plain sight – 1Password
[8] Ransomware: The True Cost to Business – Cybereason
[9] The State of Web Application and API Protection – Radware
[10] State of Software Security : Volume 11 – Veracode
[12] 2020 IoT Threat Report – Unit 42 Palo Alto Networks
[13] OT/IoT Security Report – Supply Chain and Persistent Ransomware Attacks Reach New Heights – Nozomi Networks
[14] 2021 State of the Phish – Proofpoint
[15] Attack landscape Update – H1 2021 – F-Secure
