
We can’t talk about social engineering without mentioning phishing. Similarly, email is essential when it comes to phishing. Although there are other social engineering techniques, such as vishing, and multiple phishing vectors, such as SMS (smishing), email remains the preferred tool of attackers.
In this article, we will present three tools commonly used to carry out phishing campaigns: Gophish, Evilginx and Evilgophish.
Before diving into the practical details and compromising a Dropbox account in three different ways (a test account, of course), let’s take a step back to explain two approaches to phishing on which these tools are based.
Phishing Techniques: Clone and Man in the Middle (MitM)
A few clarifications before we begin. In the rest of this article, we’ll be talking about phishing for Dropbox access. That said:
- Not all phishing emails are aimed at recovering a company’s VPN or webmail credentials.
- Not all phishing attempts target employees of the same company. Some attacks are aimed at mass distribution of malware, such as the RedLine stealer a few years ago. Most phishing attacks are opportunistic.
- At the end of the article, we will look at smishing, which is “phishing by SMS”. As mentioned in the introduction, several vectors can be used for phishing (email, SMS, Teams, Discord, etc.), email being the most common. Phishing is often associated with email, but it doesn’t really matter which channel is used. It should be referred to as “*-ishing”. In the remainder of this article, we will specify “phishing by email” where this is important.
Clone phishing
The principle of clone phishing is simple. The attacker copies a known login form (such as the company’s VPN authentication page), hosts it on his server, and then sends fraudulent links (by email, for example) redirecting to this fake form.
However, this method has its drawbacks. Copying the interface is easy. The attacker downloads the resources (HTML, JS, CSS) of the legitimate form and replaces the references to the original site to make the clone independent. But this process can be tedious depending on the number of resources.
In addition, any changes to the legitimate interface must be replicated on the clone to maintain an exact copy and a realistic scenario.
Another challenge is multi-step authentication (not to mention multi-factor authentication); a first page for the email address, then a second for the password. In this case, the attacker has to clone each page and chain them together, which complicates the task. However, cloning the password page is generally sufficient to recover the password, as the email address is generally known.
The main disadvantage of clone phishing is strong authentication. Two-factor authentication (codes sent by SMS, generated by a mobile application, etc.) pose a problem.
If the cloned form requires double authentication, the attacker must also clone the form for entering the one-time password (OTP). Alternatively, they can add a field for the OTP on the fake form, but this may arouse suspicion.
After recovering the OTP entered on the fake form, the attacker must quickly replay it on the legitimate site to access the victim’s account. OTPs, often TOTPs (Time-based One-Time Password), are valid for a limited period (30 or 60 seconds), reducing the attacker’s window of opportunity.
In short, clone phishing is effective if the target form is not too complex and does not have double authentication.
However, the attacker does not need to authenticate himself in place of his victim. He can capture the victim’s session tokens (cookies, for example). This idea is the basis of a more advanced and increasingly widespread phishing technique: Man in the Middle (MitM) phishing.
Man in the Middle (MitM) phishing
Man in the Middle (MitM) phishing, or reverse-proxy phishing, involves the attacker placing his server between the victim and the legitimate site.
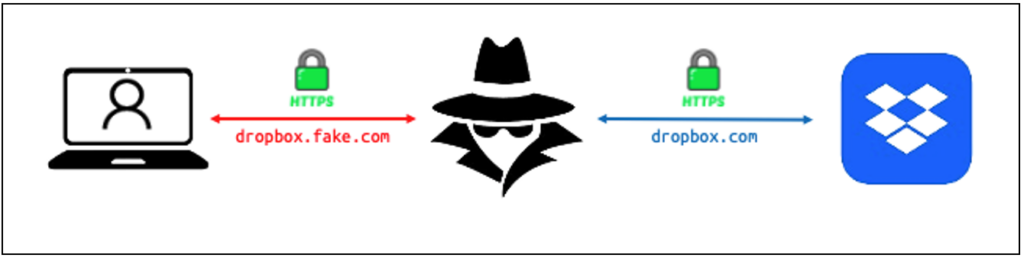
To do this, the phishing link points to a malicious domain (for example, dropbox.fake.com) which acts as a proxy to the legitimate app (in this case, dropbox.com).
The user interacts almost normally, but the attacker gains access to all traffic, including passwords and double authentication codes.
After authentication, a session token is issued to the user. This token is also accessible to the attacker, who can import it into his own browser to access the victim’s account.
The attacker is then connected to the same session as the user. If one of them disconnects, so will the other. To persist on the victim’s account (even after the victim has logged out), the attacker can add a trusted device to generate valid double authentication codes or recover the account recovery codes (if available).
Compared with clone phishing, MitM phishing has several advantages:
- It enables more realistic attacks to be constructed, even for applications with multi-factor authentication.
- It is not affected by interface modifications, as the user interacts directly with the legitimate site via the attacker’s server.
- MiTM phishing bypasses most two-factor authentication methods. The attacker does not need to authenticate in the victim’s place as he has access to the session tokens. However, certain strong authentication methods, such as hardware keys (YubKey) or software keys (passkeys), take into account the identity of the remote site and offer effective protection. For example, authenticating on dropbox.fake.com is not the same as authenticating on dropbox.com.
Practical Application of Phishing Techniques: Stealing Dropbox Credentials
Let’s get down to the real business by presenting a few tools that put the techniques presented into practice.
Here is a brief outline of the scenario inspired by one of our audits. Our objective is to access a Dropbox test account, on which Two-factor authentication is activated. The phishing email sent to the “victim” mentions the end of the Dropbox subscription and the loss of file synchronisation to encourage him to authenticate. The malicious domain used is “dropbox.fake.com”.
Let’s see how this scenario plays out depending on the technique used.
Clone phishing with Gophish
Gophish is an open-source solution designed to help pentesters and companies run phishing simulations. It offers a web interface that makes it easy to configure and send a campaign.
Rather than a long speech, here’s a video showing the complete Gophish attack:
Let’s take a step-by-step look at the attack (the video starts at step 3):
- Cloning the authentication interface: the attacker clones the Dropbox login interface. There are two forms: the first for the email address, and the second for the password. The attacker only clones the second form by pre-filling the known email address (recovered during the reconnaissance phase) to gain credibility.
- Configuring the campaign in Gophish: the attacker configures the campaign, specifying the target email addresses, the content of the email, the SMTP configuration and the cloned authentication form.
- Sending the malicious email: the attacker sends the email from Gophish, containing a pretext encouraging the victim to authenticate quickly and a link to the fake form.
- Receipt of the email by the victim: the victim receives the email and clicks on the link because of the convincing pretext and/or lack of awareness.
- Password submission by the victim: the victim enters his password on the fake authentication page (hosted on “dropbox.fake.com”). After entering the password, the victim remains stuck on the form or is redirected to an error page to maintain the illusion.
- Password recovery by the attacker: the attacker recovers the password from Gophish and attempts to authenticate on the legitimate “dropbox.com” site.
- Blocked by the two-factor authentication: with this feature enabled, the attacker cannot complete the authentication process, as he cannot produce a valid 2FA code without access to the victim’s phone. Without double authentication, the account would have been completely compromised.
As we have seen, clone phishing (using Gophish, for example) does not make it easy to bypass dual authentication. For a more effective method, attackers can turn to Man in the Middle phishing.
Man in the Middle phishing with Evilginx
Evilginx is a reverse-proxy phishing kit designed for pentesters and red teamers. It enables to bypass double authentication by focusing on user session tokens. Since version 3.3, Evilginx can be integrated with Gophish to use its web interface and make it easier to send campaigns.
Let’s take a look at how the same attack works, this time with Evilginx:
- Email configuration and delivery: after configuring the campaign in Gophish, the attacker sends an email containing a link to Evilginx.
- Victim clicks: the victim receives the email and clicks on the link to Evilginx.
- Interaction via Evilginx: Evilginx acts as a reverse proxy between the victim’s browser and the legitimate “dropbox.com” site. The victim enters their email address and password, and validates double authentication in the usual Dropbox interface. Meanwhile, the attacker has access to all traffic.
- Recovery of tokens: once the victim has been authenticated, the attacker recovers the session tokens from the Evilginx terminal (not shown in the video) and imports them into his own browser.
- Account access: the attacker opens the legitimate Dropbox site and automatically accesses the victim’s account using the stolen cookies.
As has been shown, MitM phishing is a way to bypass double authentication (in most cases). However, two-factor authentication remains a crucial security mechanism, particularly against clone phishing. At the end of this article, we’ll also look at the mechanisms for protecting against MitM phishing.
Let’s now take a look at the same attack in MitM, but this time delivered by SMS, using Evilgophish.
MitM Smishing with Evilgophish
Evilgophish combines Evilginx and Gophish, adding features such as sending SMS via the Twilio API.
Here’s how the attack works on the victim’s side:
From the attacker’s point of view, after recovering the session cookies in Evilginx:
The behaviour differs slightly from that of Evilginx:
- An error is displayed in the victim’s browser after he enters the 2FA code. However, Evilginx has already recovered the session cookies, so this error is not blocking.
- A second error occurs when the attacker attempts to access the victim’s account after importing the stolen cookies. However, password-only authentication becomes possible thanks to the cookie issued if the user has ticked the “Trusted device” box. Even if the victim has not ticked this box (as shown in the video), the attacker, controlling the traffic, can force certain settings, thus bypassing the user’s choices.
Technical Protection Against Phishing
To conclude, let’s take a moment to look at how an application can protect itself against clone phishing and, more specifically, against MitM phishing.
Client-side protections
One initial idea is to implement protections in the JavaScript code of the application, running in the client’s browser.
A common protection consists of verifying the identity of the site on which the code is executing, for example:
function validateHostname() {
return window.location.hostname.endsWith("dropbox.com");
}The phishing domain is generally different from the legitimate domain (for example, dropbox.fake.com), so the verification will fail if the user visits the fraudulent site.
However, it must be kept in mind that any client-side protection is vulnerable, as the attacker can modify the JavaScript code of the page. Whether the attacker is in a Man in the Middle position or using a clone, they can remove the call to the validateHostname function or render it inoperative (always returning true).
In practice, the JavaScript code can be obfuscated, making the task more complex for the attacker, if not impossible. The cost then becomes too high for the attacker, who will prefer to target another application.
A more recent variant involves using encrypted tokens to validate the identity of the site server-side. When the user submits their password, an encrypted token (containing, for example, the value of window.location.hostname) is added to the request by JavaScript code. Upon receiving the request, the server decrypts the token and verifies the identity of the site visited by the initial client.
This method can also be bypassed by the attacker if they identify the JavaScript code constructing the token. They would then simply need to replace window.location.hostname with the string ‘dropbox.com’ when constructing the token to pass the server-side validation. That said, the complexity and obfuscation of the JavaScript code can once again make this task impossible within a reasonable time frame for an attacker seeking quick profit.
Server-side protections
In addition to JavaScript verifications, there are several server-side protections against phishing in MitM mode.
For example, Microsoft Entra ID (formerly Azure Active Directory) uses conditional access, based on various risk factors, to determine if an authentication request is legitimate (such as geographic origin, browser characteristics, etc.).
This works because the legitimate user’s requests are relayed by the attacker’s server, which acts as a client to the legitimate application.
The IP address visible from the application is that of the attacker’s server, not that of the victim. Moreover, since the attacker establishes a new HTTPS connection with the application, certain characteristics of the exchanges may be suspicious. For example, the TLS versions or encryption suites proposed by the malicious client may differ from those of a typical browser (like Chrome or Firefox) which have a known fingerprint (JA4 fingerprint). This can help detect a phishing server in reverse proxy mode.
Depending on the identified risk, the application may require a stronger authentication method (such as TOTP or a security key) or even block access. For example, Microsoft Entra ID can impose a minimum authentication level based on the identified risk level for a user attempting to authenticate.
Conclusion
Phishing is one of the most used vectors by attackers because sending an email or SMS can have a potentially significant, even critical impact, or at least gain initial access.
In the cybercriminal world, there are now several Phishing as a Service offers, such as Evilproxy (launched at the end of 2021, four years after the release of Evilginx), NakedPages, and Tycoon. These services democratise advanced phishing techniques, called Adversary in the Middle (AitM), enabling less experienced attackers to bypass advanced protections like two-factor authentication.
It’s an eternal race between attackers’ offensives and the defences put in place. Attackers constantly innovate with increasingly sophisticated techniques as protections become more robust, and vice versa. Innovations are even faster since phishing is a very widespread attack vector.
The human element, often considered the weak link, is actually one of the first links to secure so that it becomes an asset and not a weakness. Effective employee awareness, combined with technical measures, significantly reduces the risk of phishing.
Author: Benjamin BOUILHAC – Pentester @Vaadata
