Traditional firewalls protect IT environments against external attacks, by allowing and blocking connections to certain areas.
These firewalls control incoming and outgoing network traffic, based on a set of rules.
Here is a basic example:
Let’s suppose your company has a web server inside its infrastructure. In order for the web server to be reachable from outside your company, some rules will have to be established to authorize web traffic to and from that server.
Some “ports” will be open, on a given IP address (the one of your server).
Your company can choose to allow web traffic only, or allow other traffic according to its needs.
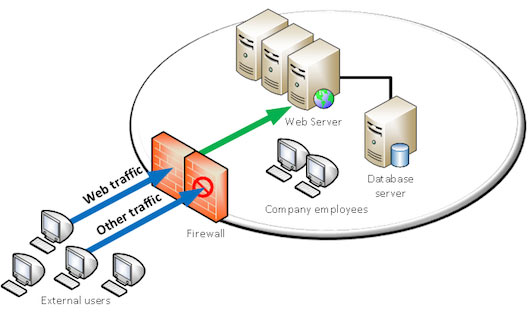
In our example, allowing web traffic only does not guarantee that this traffic is safe.
The web has enabled many possibilities and allowed easy access to resources and data. Unfortunately, web technologies are not completely safe by nature and threats are as numerous as opportunities. Traditional firewalls cannot analyze in details what is reaching the server.
By opening communication channels to web servers, the door is also open to new threats: application attacks.
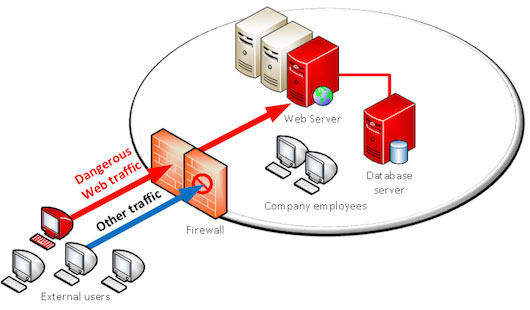
The web traffic can embed many types of attacks: SQL injections, Cross Site Scripting, Cross Site Request Forgery, session hijacking attacks… hundreds of possible attacks.
This is where web application firewalls (WAF) have their role to play.
By analyzing web traffic, and with a smart detection engine, web application firewalls are able to distinguish dangerous from legitimate traffic and block attacks.
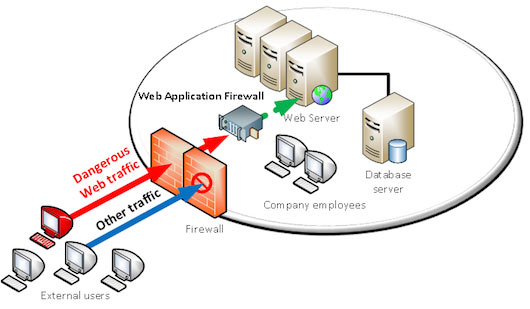
From a technical standpoint and referring to the OSI model (conceptual model describing communication system layers), traditional firewalls act on the three first layers (physical to network layers), and web application firewalls act on the seventh layer (application layer).
