
Active Directory (AD) is at the heart of many organisations’ IT infrastructure. It manages authentication, authorisation and access to critical resources within a network.
However, its complexity and importance make it a prime target for attackers. A single vulnerability in an Active Directory can enable an attacker to quickly compromise an organisation’s entire network.
To prevent these risks, Active Directory pentesting (AD penetration testing) has become an indispensable tool. This offensive approach involves simulating attacks to identify and correct exploitable vulnerabilities.
This article explores the objectives and methodology of an AD penetration test. Through use cases, we detail the black box (unauthenticated) and grey box (authenticated) testing approaches.
Comprehensive Guide to Active Directory Penetration Testing
- What is Active Directory Pentesting?
- Scope of an Active Directory Penetration Test
- Active Directory Pentesting Methodology
- Perform an Active Directory Penetration Test with Vaadata, a Company Specialised in Offensive Security
What is Active Directory Pentesting?
An Active Directory penetration test consists of assessing the security of an AD environment by simulating realistic attacks. The aim is to identify exploitable vulnerabilities that could compromise the entire internal network. This type of test focuses on authentication mechanisms, rights management and the protection of sensitive data.
Active Directory pentesting also aim to analyse the configuration of domain controllers, the security policies applied and user-related vulnerabilities. By replicating the techniques used by attackers, they can highlight often invisible vulnerabilities, assess their impact and suggest corrective measures to strengthen network security.
Scope of an Active Directory Penetration Test
The scope of an Active Directory penetration test is determined according to the needs and objectives of the client organisation. It can cover the entire AD infrastructure or be limited to specific segments, such as a particular domain or subnet.
For example, the tests cover (non-exhaustive list):
- Domain controllers: Analysis of main servers, system configurations, and critical services such as DNS, LDAP and Kerberos.
- Users and groups: Evaluation of user accounts, assigned permissions, and high-privilege groups (such as administrators).
- Security policies: Check password policies, access restrictions, etc.
- Network shares: Identification of accessible shares, exposed sensitive files and misconfigured permissions.
- Exposed interfaces: Tests on externally accessible services, such as VPN portals, RDP access or hybrid environments (Azure AD).
An AD penetration test can also include an assessment of logging and monitoring mechanisms, to measure the company’s ability to detect an intrusion attempt.
Active Directory Pentesting Methodology
An Active Directory penetration test consists of two distinct phases. The first is a reconnaissance phase. It aims to gather both human and technical information about the target organisation.
The second is the exploitation phase. This can be either black box or grey box. The aim is to compromise the internal network to gain access to the domain administrator account.
Let’s imagine a scenario where an attacker gains access to the internal network via a connection to the company’s Wi-Fi. This type of situation can easily happen if the password policy for Wi-Fi is weak. The risk is even higher if there are no network partitions.
Human and technical recon
This phase is essential for the attacker, as it enables him to gather critical information about the target infrastructure before starting exploitation actions. It includes an analysis of the human and technical aspects.
In an Active Directory penetration test, in-depth reconnaissance is essential. It ensures complete identification of vulnerabilities that could subsequently be exploited.
Human recon
The attacker’s objective is to identify potential users with accounts on the company’s internal network, focusing particularly on IT department employees.
To do this, he gathers public information such as first and last names. This data is often available on platforms such as LinkedIn.
Once the list of users has been compiled, the attacker can check whether these accounts exist in the Active Directory domain. Tools such as Kerbrute enable this step to be carried out efficiently.
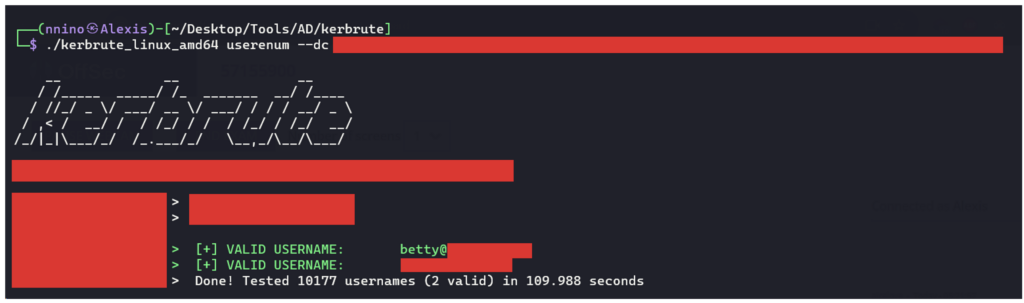
The attacker can then check whether certain valid accounts are ‘ASREPRoastable’. The aim is to request a TGT (Ticket Granting Ticket) for these users and attempt to crack the offline session keys. This could give him access to the targeted accounts.
Other techniques can be used during this human-focused reconnaissance phase. For example, the attacker can search for the passwords associated with the accounts by exploring public databases leaked by the target organisation.
Technical recon
When exploring the internal network, the attacker seeks to identify the machines and elements present. To do this, it exploits the characteristics of network protocols to locate connected devices and detect any sub-networks.
Once the sub-networks have been identified and the machines located, the attacker scans the ports and services. This identifies the services exposed and their versions. By comparing this information with vulnerability databases (CVEs), the attacker can identify vulnerable services and plan how to exploit them.
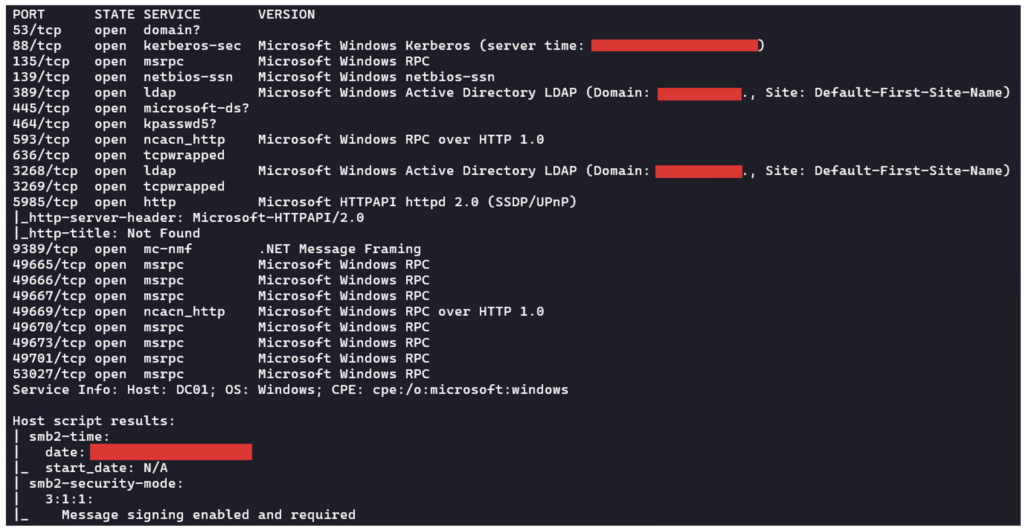
Even without valid access to the domain, an attacker can gather essential information to prepare other types of attack. This includes details of operating system versions, SMB configuration and other network characteristics.
With this data in hand, the attacker can analyse the vulnerabilities identified and define the most effective strategies for the exploitation phase.
The exploitation phase takes place in two stages: the first in ‘unauthenticated’ mode (black box) and the second in ‘authenticated’ mode (grey box).
In this scenario, the attacker gained access to the internal network by compromising the company’s Wi-Fi. This implies that he was physically present on site, but that he does not yet have a valid domain account in the Active Directory.
His first objective will therefore be to find a way of obtaining valid access to the domain.
Black Box Penetration Testing of an Active Directory
Common Vulnerabilities and Exposures (CVEs) testing
Black-box exploitation of an Active Directory domain often begins by examining the following known major vulnerabilities (CVEs):
- Zerologon (CVE-2020-1472)
- EternalBlue / BlueKeep (MS17-010 / CVE-2019-0708)
- PetitPotam pre-auth (CVE-2022-26925)
- SMBGhost (CVE-2020-0796)
It is crucial to test for these vulnerabilities, as many Windows Server machines are not always up to date with the latest patches or security versions. They can offer the attacker the possibility of fully compromising the company’s Active Directory domain.
If these vulnerabilities do not allow the system to be exploited, it is necessary to look for improper configurations. By default, Windows often leaves doors open, providing additional opportunities for an attacker.
Identifying improper configurations
DHCPv6 spoofing/poisoning
By default, in Windows environments, IPv6 is enabled and takes precedence over IPv4. However, as IPv6 is often unused or misconfigured, when a Windows machine starts up or connects to the network, it sends a DHCPv6 request to obtain configuration.
Since DHCPv6 works in multicast mode, an attacker present on the same network can respond to these requests and provide machines with a personalised IP configuration.
LLMNR, NBT-NS and mDNS spoofing
In Windows environments, multicast name resolution protocols are enabled by default, such as LLMNR (Local-Link Multicast Name Resolution), NBT-NS (NetBIOS Name Service) and mDNS (multicast Domain Name System). When standard name resolution protocols fail, Windows systems try to resolve names in this order: DNS, LLMNR, then NBT-NS.
An attacker can exploit this feature by responding to multicast or broadcast requests. Victims are then redirected to the attacker, who asks them to authenticate themselves in order to access the requested resources.
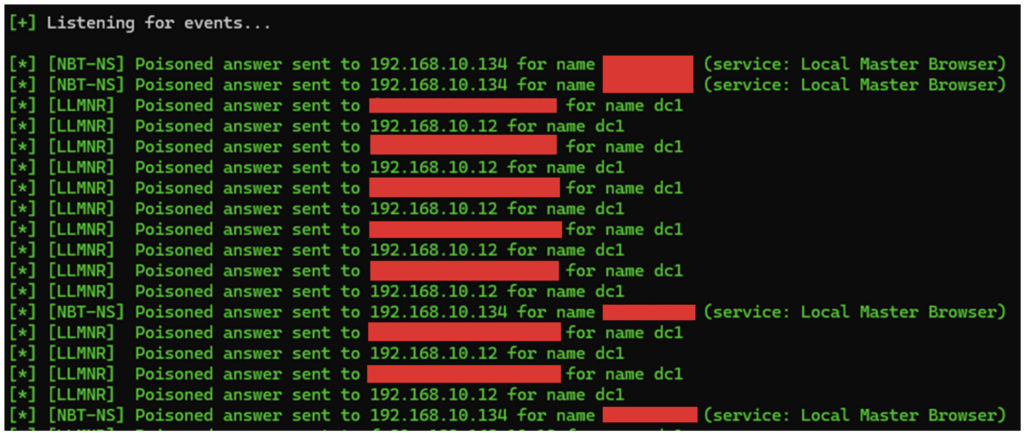
Depending on the misconfigurations present, our attacker could use them to relay authentications received on services such as SMB, MSSQL, LDAP, etc.
Kerberoast w/o pre-authentication
If an attacker knows of an account for which pre-authentication is not required (i.e. an ASREProastable account), as well as one or more service accounts to target, he can launch a Kerberoast attack without needing to control an Active Directory account (since pre-authentication is not required).
It is important to note that the attacker could also use traditional network attacks, such as ARP spoofing/poisoning.
At the same time, the attacker will attempt to exploit ‘null / anonymous sessions’ on the SMB protocol, which could enable him to enumerate network shares and obtain information about the configuration of the Active Directory.
Other tests can be carried out, such as authentication attempts on previously identified domain accounts or brute force on hashes recovered during network attacks.
Grey Box Penetration Testing of an Active Directory
CVEs exploitation
Once an attacker has a valid account in the Active Directory domain, he can target the exploitation of vulnerabilities and misconfigurations more precisely.
In addition to the CVEs identified during the black box phase, several other vulnerabilities can be exploited when a valid account is used:
- SamAccountName Spoofing (CVE-2021-42278 / CVE-2021-42287)
- PrintNightmare (CVE-2021-1675 / CVE-2021-34527)
- Credentials Roaming (CVE-2022-30170)
- Bronze Bit (CVE-2020-17049)
- GoldenPac (CVE-2014-6324)
Enumerating objects and permissions
A crucial grey-box step is to enumerate objects and permissions in the Active Directory. To do this, tools such as BloodHound are frequently used to map relationships and privileges within the domain.
This tool allows the attacker to visualise the privilege escalation paths leading to administrative control of the domain, including those that allow propagation via delegations, privileged groups or trusted relationships between domain controllers.
During this phase, a misconfigured Active Directory provides the attacker with many potential attack vectors to exploit.
Abusing DACLs (Discretionary Access Control Lists)
DACLs are lists made up of ACEs (Access Control Entries). These identify the users and groups to whom access to an object is authorised or denied.
When misconfigured, these ACEs can be exploited by an attacker to perform a lateral movement or privilege escalation.
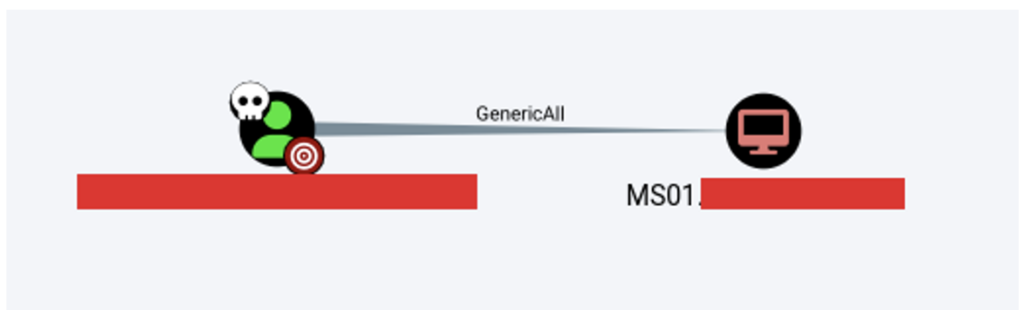
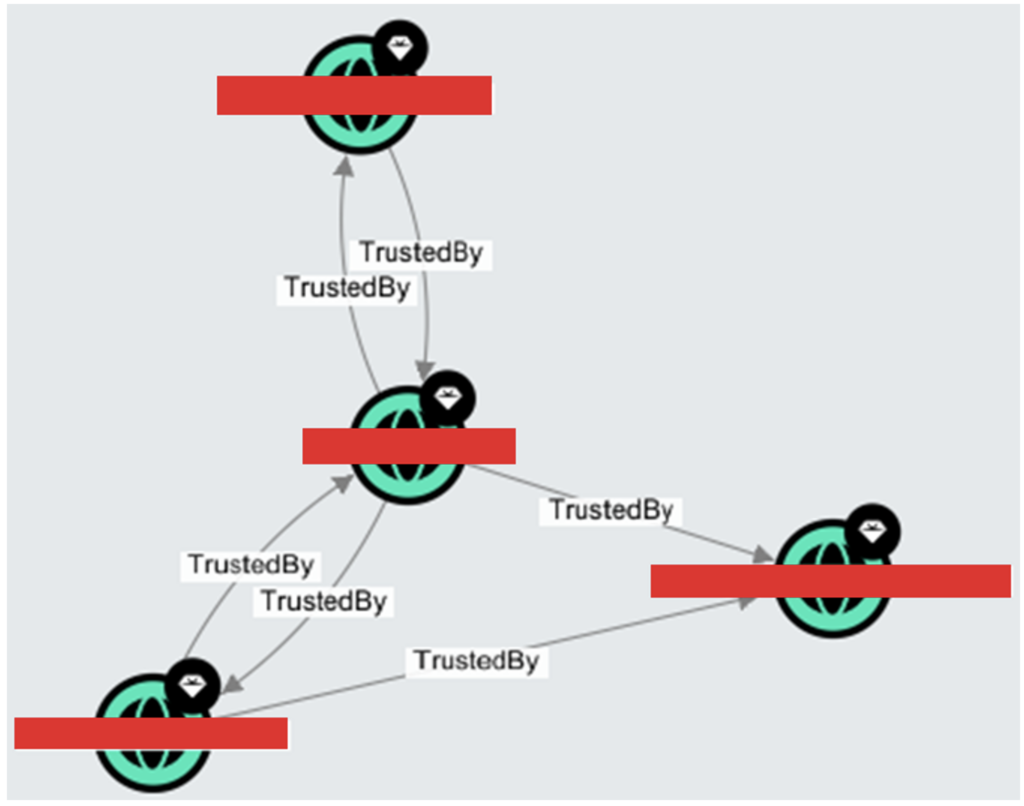
Abuse of trusts
Trusts allow one domain to grant access rights to another, facilitating the exchange of information.
However, if these trust relationships are misconfigured, an attacker can exploit them to access sensitive resources or escalate privileges.
By abusing a poorly secured trust, it becomes possible to bypass security controls and extend access to the organisation’s networks or sensitive data.
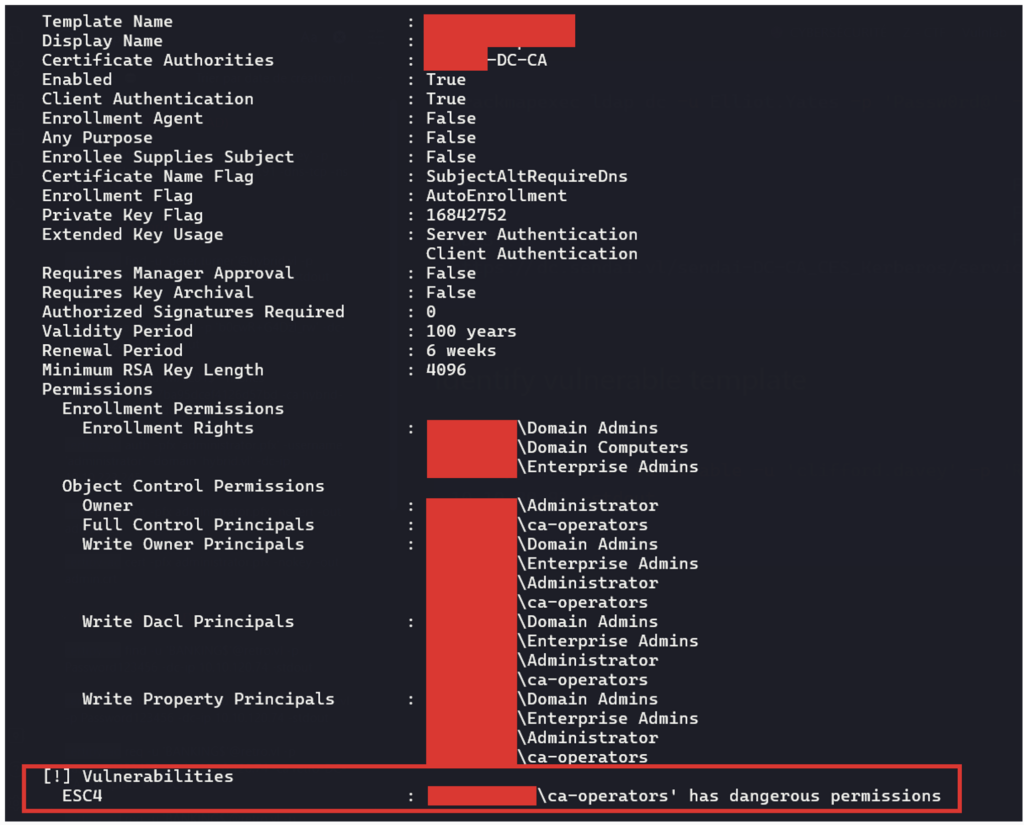
Exploiting AD CS (Active Directory Certificate Services)
AD CS (Active Directory Certificate Services) is a Public Key Infrastructure (PKI) used for encryption, digital certificates and signing.
If this service is misconfigured, an attacker could take advantage of it to request certificates, impersonate a privileged user or obtain an authentication certificate for a specific server.
Once an attacker has obtained a valid account in the Active Directory domain, there are a multitude of additional attacks he could attempt.
It is therefore difficult, if not impossible, to be exhaustive or even synthetic about all the possible attacks, as there are so many of them.
Perform an Active Directory Penetration Test with Vaadata, a Company Specialised in Offensive Security
It is important to assess the level of resistance of your Active Directory to the attacks described above.
This assessment can be carried out using one of the audits we offer. Whether black box or grey box, we can identify all the vulnerabilities in your AD and help you fix them.
Authors: Alexis PARET – Pentester & Amin TRAORÉ – CMO @Vaadata

