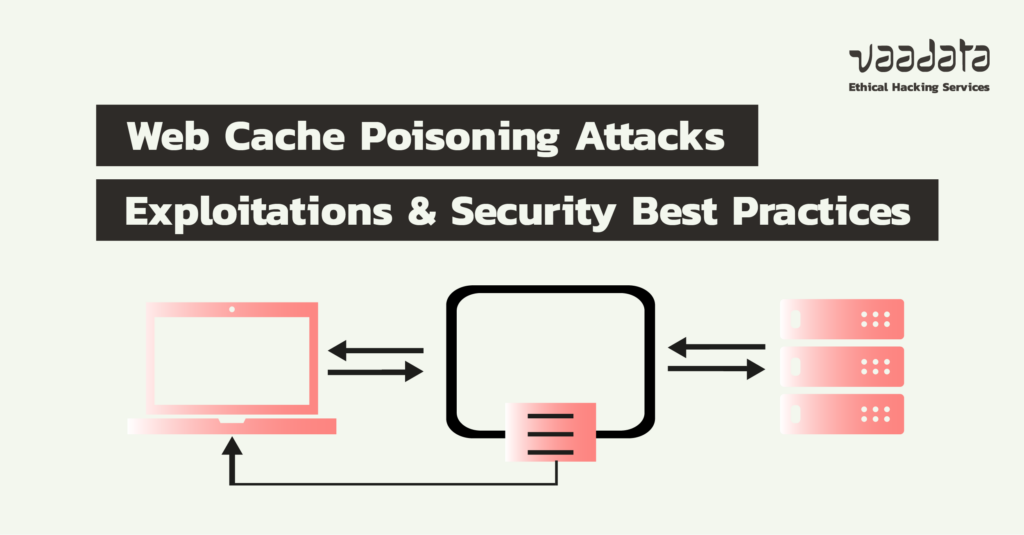
To improve the display speed of web pages and lighten server loads, many companies rely on caching mechanisms.
This system enables frequently requested resources (such as images, scripts or HTML pages) to be stored temporarily, so that they can be served up more quickly on subsequent requests.