Abraham Lincoln (repeating a woodsman) would have answered the question: what would you do if you had just six hours to chop down a tree? I would spend the first four hours sharpening my axe.

What does it tell us? That preparation is key.
You cannot protect what you don’t know, therefore knowing your attack surface is the first essential step to protect it efficiently.
What is an Attack Surface?
An attack surface consists of all elements that might be attacked to cause a security incident.
There are generally two types of attack surface considered: the digital and the physical attack surface.
While the digital attack surface comprises, for example, web services, network, communication protocols, domain names… the physical attack surface involves the physical points of attacks against a company, such as the windows of buildings, production facilities, or even a fire…
These two attack surfaces are overlapping and interconnected; it is equally important to secure both of them.
In this article, we focus on the attack surface of an information system.
It can be divided in two:
- the external attack surface, which includes all points accessible remotely from the internet,
- the internal attack surface, which includes all points accessible from inside the company.
How to Know Your Attack Surface?
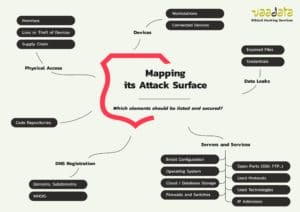
Mapping the attack surface of your information system is a task that requires to think about all your different assets and about the value they have or they can enable to access to.
To create a global mapping, it involves to:
- List
- your DNS records (domains, sub-domains),
- your exposed servers and services (SSH, FTP…)
- applications used and their versions (this encompasses your own applications and third-party ones).
- Take into consideration the physical access to the company’s assets (buildings, theft of devices, production line…),
- And other elements depending on your specific situation.
You can download this overview of the main elements to list and to secure when you’re mapping your attack surface. This overview is only a non-exhaustive base, as each context has specific elements to take into account.
There are various tools and search engines that exist to help you with the mapping: shodan.io, censys.io, crt.sh…
For example, shodan.io enables to verify which of your devices of your network are available from the internet (servers, routers, printers…), whereas crt.sh can find from a url all certificates related to a name or a brand.
Knowing its attack surface is sometimes more complicated than expected because of shadow IT. Shadow IT refers to the IT devices and tools used by employees without the knowledge and approval of the IT department. These solutions are therefore not controlled, in particular, regarding their security, and can bring vulnerabilities to the information system or cause a data breach.
Some shadow IT elements can be traced back during the mapping of the attack surface (connected devices connected to the network without authorisation for example), but other elements, such as web services, are harder to detect.
How to Reduce your Attack Surface?
Once you know your attack surface, you can manage it and assess the associated risks. When the attack surface is important, the inventory also helps you to prioritise the elements to protect.
The aim of knowing your attack surface is to then be able to reduce it (when possible) and put in place relevant protection.
Having the less possible attack points allows focusing the protection efforts and therefore strengthening their security.
To reduce your attack surface, general advice is:
- to clean or delete all elements that are not used any more,
- to segment the network,
- to monitor network and logs,
- to make some tools and services only available through VPN or through authentication,
- to follow the principle of least privilege,
- to raise awareness of the staff about risks they are facing (including social engineering)
Keeping the Attack Surface Up To Date
Once the mapping and reduction of the attack surface have been done, the following step, as important as the previous ones, is to keep it up to date, in order to continue to monitor and to protect it.
In order to do this, it is necessary to follow the new services implemented, the evolution of the infrastructure, but also to monitor the release of vulnerabilities, patches, fixes… in order to apply them when changes concerning your assets are required.
An IT Asset Management tool can help you to centralise and monitor information about your attack surface.