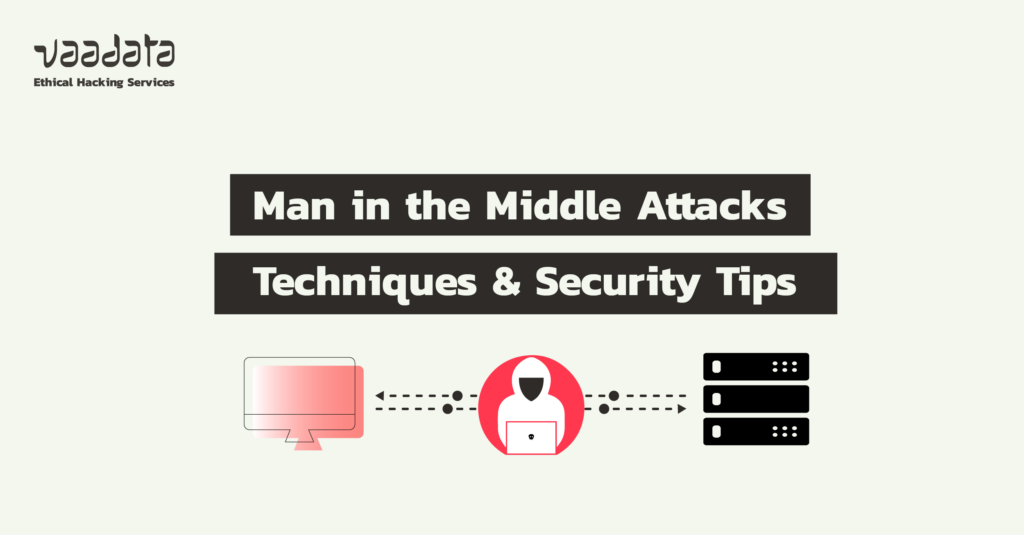
Before discussing techniques and tools, it is essential to define the ‘secrets’ sought during penetration tests.
These secrets are generally private character strings which, if compromised, can be used to access a system, break encryption or forge data useful for authentication. Examples include a username and password pair, API keys, private keys or a session token that is still valid.