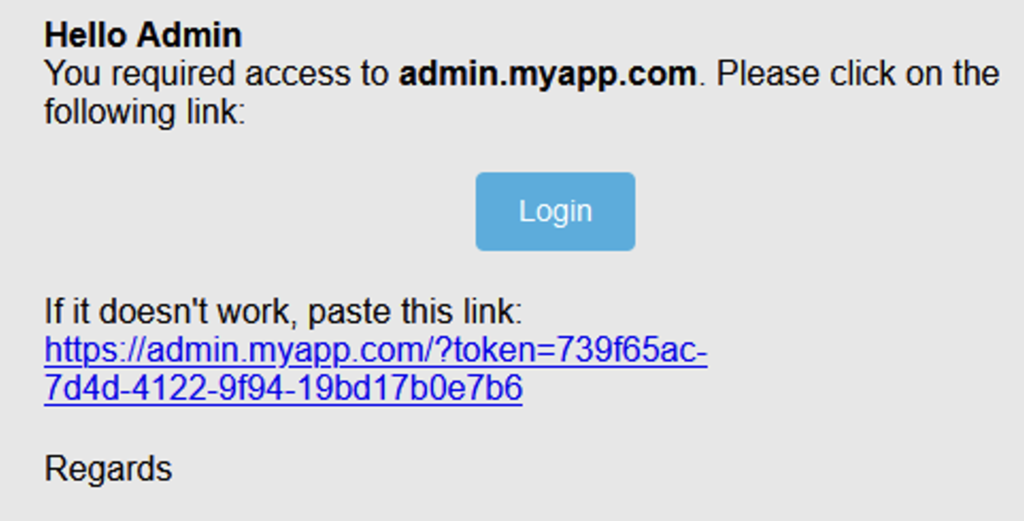
Faced with an ever-increasing number of internal attacks, network infrastructure security is a key factor in ensuring the confidentiality and integrity of data, as well as the continuity of an organization’s activities.
There are several ways of assessing the security of an internal network. In this article, we present the “offensive” approach, which we believe to be the most effective: internal penetration testing. We detail the principles and objectives, as well as use cases for black box and grey box penetration testing of an internal network.